Hopefully you must get an idea now! about the topics to be covered in the further classes.
Facilitator Guide
Please Fill Out The Attendance Form
Let's start with the recap of computing skills - Part -1 that you must have done in previous semesters.
Recap of computing skills - Part - I
MS-Excel Practice Exercise
Create and share Google sheets for below work
Try these shortcuts to create Google sheet
Qs 1. What all are the features of MS-Excel that make it so popular?
Qs 2. What all we can do using MS-Excel
Qs 3. Define each component of this image.
Qs 4. Create this Google sheet
Qs 5. Create Student Details sheet with below fields.
Qs 6. Create pocket money calculator ?
QS 17. Apply below functionalities.
Apply below listed operations on family budget sheet.
1)Apply filter
2) Create pie chart only
3) Protect sheet
4) Add suitable comment on savings
5)Ensure your sheet must be
grammatically okay.
6)Reflect highly outgoing item of
Feb month
7)Sort the outgoings in descending
order
8)Create macro to calculate annual
savings
9)Apply goal seek to monthly
budget
10) Ensure your datasheet must not
have duplicates
11)Calculate annual savings using
consolidate feature only!
Instructions :
- Save
the file under the name stationary
- Calculate
the cost value of the first article by using the formula Qty X price and
then copy the formula to the other cells.
Calculate the total cost value spent by you as per the sheet.
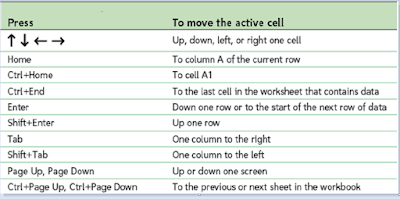
Qs 22. Practice all these Worksheet Navigation Keys.
Qs 23. Working with Formulas
Qs 1. Prepare dynamic Presentation out of this rough draft.
Instructions:
- Use
your own creativity to make this presentation effective.
- Write
your name after efforts by :
- Your
presentation will be scaled between
1-10 marks.
- Use
selective color scheme.
- Use
appropriate graphics to make your presentation eye catchy.
Slide -7
¡ Put Your name, date, and slide number at the footer of each slide.
¡ Once you are done with your slides, view your Slide Show. Add Custom or Preset Animation and Sounds (go to Slide Show, Preset Animation or Custom Animation).
¡Change the theme of your slides as per your content [Download templates from PowerPoint Templates for Presentations (slidemodel.com)] or
[Eye Catching Color Free PowerPoint Template and Google Slides Theme (pptmon.com)] or
[Eye catching powerpoint templates | Prezi] or
🖧[Free Creative Google Slide and PowerPoint templates (slidesgo.com)]
¡ Save your presentation twice: the first time as a PPT presentation and the second time as a Web Page.
¡ Create a Print Preview
¡ Show your presentation in PowerPoint and web page formats and the Print Preview to the instructor.
Qs 2. Prepare presentation on Famous
personalities of India [Choose any one topic]
¡ Narendra
Modi
¡ Shahrukh
Khan.
¡ Aamir
Khan.
¡ Virat
Kohli.
¡ Mary
Kom.
¡ Mukesh
Ambani.
¡ Arvind
Kejriwal
¡ Kapil
Sharma
¡ Baba
Ramdev
¡ Sachin tendulakar or Virat Kohli
Qs 3. Explore your life goals and prepare an effective presentation for achieving the Goals of your life.
Formula to achieve your goal.
CAREER: Where
do you hope to be in your career development at the time of your graduation?
Examples:
•
I will be starting my career in advertising
with an entry-level copywriting position in a large advertising firm.
• I will be continuing my education in a Ph.D. program in Biochemistry to eventually become a university professor. or I will be working as a pediatric nurse in an urban hospital somewhere in California.
§ What you want to BE
§ What
you want to LEARN
§ What
you want to DO
§ What
you want to HAVE
§ What you want to GIVE
After completion of this topic , candidate will be familiar with the : Latest trends and technologies in upcoming fields in ICT. Will be able to understand need of Cyber Security and will be able to secure their PC and Mobile devices by using basic security features.
"Cyber law is any law that applies to the internet and internet-related technologies & is one of the newest areas of the legal system."
- Cyber law is any law that applies to the internet and internet-related technologies.
- This is because internet technology develops at such a rapid pace.
- Cyber law provides legal protections to people using the internet. This includes both businesses and everyday citizens.
- Understanding cyber law is of the utmost importance to anyone who uses the internet. Cyber Law has also been referred to as the "law of the internet.
- Cybercrime or a computer-oriented crime is a crime that includes a computer and a network.
- The computer may have been used in the execution of a crime or it may be the target.
- Cybercrime is the use of a computer as a weapon for committing crimes such as committing fraud, identity theft, or breaching privacy.
- Cybercrime, especially through the Internet, has grown in importance as the computer has become central to every field like commerce, entertainment, and government.
- Cybercrime may endanger a person or a nation’s security and financial health.
- Offering training programs to employees.
- Hiring employees who are certified in cybersecurity.
- Being aware of new security threats.
- Cybercrimes can be committed against governments, property, and people.
- Crimes Against People. While these crimes occur online, they affect the lives of actual people. Some of these crimes include cyber harassment and stalking, distribution of child pornography, various types of spoofing, credit card fraud, human trafficking, identity theft, and online related libel or slander.
- Crimes Against Property. Some online crimes happen against property, such as a computer or server. These crimes include DDOS attacks, hacking, virus transmission, cyber and typo squatting, computer vandalism, copyright infringement, and IPR violations
- Crimes Against Government. When a cybercrime is committed against the government, it is considered an attack on that nation's sovereignty and an act of war. Cybercrimes against the government include hacking, accessing confidential information, cyber warfare, cyber terrorism, and pirated software.Most of these types of cybercrimes have been addressed by the IT ACT of 2000 and the IPC. Cybercrimes under the IT ACT include:
Sec. 65, Tampering with Computer Source Documents.Sec. 66, Hacking Computer Systems and Data Alteration.Sec. 67, Publishing Obscene Information.Sec. 70, Unauthorized Access of Protected Systems.Sec. 72, Breach of Confidentiality and Privacy.Sec. 73, Publishing False Digital Signature Certificates.Special Laws and Cybercrimes under the IPC include:Sending Threating Messages by Email, Indian Penal Code (IPC) Sec. 503.Sending Defamatory Messages by Email, Indian Penal Code (IPC) Sec. 499Forgery of Electronic Records, Indian Penal Code (IPC) Sec. 463Bogus Websites & Cyber Fraud, Indian Penal Code (IPC) Sec. 420Email Spoofing, Indian Penal Code (IPC) Sec. 463Web-Jacking, Indian Penal Code (IPC) Sec. 383Email Abuse, Indian Penal Code (IPC) Sec. 500
Online Sale of Arms Under Arms Act, 1959Online Sale of Drugs Under Narcotic Drugs and Psychotropic Substances Act, 1985
Classification of Cyber Crime
Cyber Terrorism –
Cyber terrorism is the use of the computer and internet to perform violent acts that result in loss of life. This may include different type of activities either by software or hardware for threatening life of citizens. In general, Cyber terrorism can be defined as an act of terrorism committed through the use of cyberspace or computer resources.
Cyber extortion occurs when a website, e-mail server or computer system is subjected to or threatened with repeated denial of service or other attacks by malicious hackers. These hackers demand huge money in return for assurance to stop the attacks and to offer protection.
Cyber warfare is the use or targeting in a battle space or warfare context of computers, online control systems and networks. It involves both offensive and defensive operations concerning to the threat of cyber attacks, espionage and sabotage.
Internet fraud is a type of fraud or deceit which makes use of the Internet and could include hiding of information or providing incorrect information for the purpose of deceiving victims for money or property. Internet fraud is not considered a single, distinctive crime but covers a range of illegal and illicit actions that are committed in cyberspace.
This is a kind of online harassment wherein the victim is subjected to a barrage of online messages and emails. In this case, these stalkers know their victims and instead of offline stalking, they use the Internet to stalk. However, if they notice that cyber stalking is not having the desired effect, they begin offline stalking along with cyber stalking to make the victims’ lives more miserable.
For computer professionals and users, the general code of ethics is as follows.
Do’s and Don’ts for an ethical culture for computer professionals
what precaution do they promise to take with regard to cyber laws, morals and ethics.
People are unaware of their cyber rights-The Cybercrime usually happen with illiterate people around the world who are unaware about their cyber rights implemented by the government of that particular country.
Those who Commit cyber crime are anonymous for us so we cannot do anything to that person.
Every country in the world faces the challenge of cyber crime and the rate of cyber crime is increasing day by day because the people who even don’t register a case of cyber crime and this is major challenge for us as well as for authorities as well.
Committing a cyber crime is not a cup of tea for every individual. The person who commits cyber crime is a very technical person so he knows how to commit the crime and not get caught by the authorities.
In Cyber crime there is no harsh punishment in every cases. But there is harsh punishment in some cases like when somebody commits cyber terrorism in that case there is harsh punishment for that individual. But in other cases there is no harsh punishment so this factor also gives encouragement to that person who commits cyber crime.
Maintain different password and username combinations for each account and resist the temptation to write them down. Weak passwords can be easily cracked using certain attacking methods like Brute force attack, Rainbow table attack etc, So make them complex. That means combination of letters, numbers and special characters.
Always use trustworthy and highly advanced antivirus software in mobile and personal computers. This leads to the prevention of different virus attack on devices.
Always keep your social media accounts data privacy only to your friends. Also make sure only to make friends who are known to you.
Whenever you get the updates of the system software update it at the same time because sometimes the previous version can be easily attacked.
Public Wi-Fi are vulnerable. Avoid conducting financial or corporate transactions on these networks.
A computer get infected by malware attacks and other forms of cybercrime is via email attachments in spam emails. Never open an attachment from a sender you do not know.
Operating system should be updated regularly when it comes to internet security. This can become a potential threat when cybercriminals exploit flaws in the system.
Cyber law is increasing in importance every single year. This is because cybercrime is increasing. To fight these crimes, there have been recent trends in cyber law. These trends include the following:
- New and more stringent regulations.
- Reinforcing current laws.
- Increased awareness of privacy issues.
- Cloud computing.
- How virtual currency might be vulnerable to crime.
- Usage of data analytics.
Creating awareness of these issues will be a primary focus of governments and cyber law agencies in the very near future. India, for instance, funded cyber trend research projects in both 2013 and 2014. In addition, India holds an international conference related to cyber law every year since 2014. The goal of this conference is to promote awareness and international cooperation.
An important part of cyber law is intellectual property. Intellectual property can include areas like inventions, literature, music, and businesses. It now includes digital items that are offered over the internet. IP rights related to cyber law generally fall into the following categories:
Copyright. This is the main form of IP cyber law. Copyrights provide protection to almost any piece of IP you can transmit over the internet. This can include books, music, movies, blogs, and much more.
Patents.
Patents are generally used to protect an invention. These are used on the internet for two main reasons. The first is for new software. The second is for new online business methods.
Trademarks and service marks are used the same online as they are in the real world. Trademarks will be used for websites. Service marks are used for websites that provide services.
Trade secret laws are used to protect multiple forms of IP. This includes formulas, patterns, and processes. Online businesses can use trade secret protections for many reasons. However, it does not prevent reverse engineering.
This is related to trademarks. Specifically, domain disputes are about who owns a web address. For instance, the person who runs a website may not be the person who owns it. Additionally, because domains are cheap, some people buy multiple domains hoping for a big payday.
Most people don't think contracts apply online. This is not the case. For example, when you register for a website, you usually have to agree to terms of service. This is a contract.
Online businesses are required to protect their customer's privacy. The specific law can depend on your industry. These laws become more important as more and more information is transmitted over the internet.
Some employee contract terms are linked to cyber law. This is especially true with non-disclosure and non-compete clauses. These two clauses are now often written to include the internet. It can also include how employees use their company email or other digital resources.
- Countering cyber crimes
- Software piracy
- Code of ethics - Dos and Don’ts
Copyright is an intellectual property right attached to original works in which the rightsubsists with it. Copyright is a form of protection provided by the law to the authors oforiginal works of authorship including literacy, dramatic, musical, and artistic and certainother intellectual works. This protection is available to both published and unpublishedworks. A copyright law is useful for authorship determination, duration of protection andrequirements for transfers of rights to others.
Security is an organizational concern; a business needs safeguards that protect computersystems and data from damage or unlawful use.
Privacy is an individual concern; people need assurance that their personal informationsuch as employment and credit history will be used properly.
Controls are policies, procedures, tools and techniques designed to prevent errors in data, software and systems. Access privileges, input authorization, data validations, documentation, fire alarms, training, effective communications are certain controls.
A digital signature means authentication of any electronic record by a subscriber bymeans of an electronic method or procedure. To secure data on the internet, a digitalsignature is used. It is unique to the subscriber who is affixing it so that it can be used toidentify such subscribers. It is linked to the electronic record to which it relates in such amanner that if the electronic record is altered, the digital signature would be invalidated.A digital signature uses an encryption tool to send the message that is unreadable, untilthe expected recipient uses their private key to decrypt the message.
A public key means the key of a key pair used to verify a digital signature and listed in adigital signature certificate. A private key means the key of a key pair used to create adigital signature.
Cyber law refers to all the legal and regulatory aspects of the Internet and the World WideWeb. Cyber space is governed by a system of laws and regulations called cyber law. Cyberlaw is needed because today millions of people are using the internet all over the world.Due to global communication, the Internet is misused for criminal activities which requireregulation. People with intelligence and bad intensions are misusing the Internet.
Software piracy is the unauthorized copying or distribution of copyrighted software.Software piracy can be done by copying, downloading, sharing, selling or installingmultiple copies of software onto personal or work computers. If you make more copies ofthe software or install the software more times than the license permits, upload softwarecode to a website so that others can download and use it, share software license codes oractivation keys or in some cases, share your user ID and password for a web-basedsoftware application (‘cloud’ computing), you are pirating software and breaking the law.
- Cybersecurity Research and Development.
- Threat Intelligence.
- Improved Firewalls.
- The Use of Protocols and Algorithms.
- Authentication.
- Focusing on Cloud and Mobile Security.
- Cyber Forensics.
- Realizing employees may be security risks.
- Promoting ethical and realistic security mechanisms.
- Recognizing employees that may be risks.
- Promoting awareness.
- National Cybersecurity Protection Act (NCPA).
- Cybersecurity Enhancement Act of 2014 (CEA).
- Federal Information System Modernization Act of 2014 (FISMA 2014).
- Cybersecurity Workforce Assessment Act (CWWA).
- Border Patrol Agent Pay Reform Act (BPAPRA).
- Most of these laws were meant to update existing legislation. FISMA 2014 updated the framework for security controls. NCPA was meant for information sharing between the private sector and the government.
- Who will operate the website?
- Will it be operated on site or off site?
- What security measures will be employed?
- How will email be used, and how will privacy be protected?
- It's also important that businesses monitor their IP. A good way to do this is with customer review websites. These sites can both help you identify areas for improvement and can show you if your IP is being used without your permission.
- Warren and Brandeis.
- Reasonable Expectation of Privacy Test.
- Privacy Act of 1974.
- Foreign Intelligence Surveillance Act of 1978.
- Electronic Communication Privacy Act.
- Driver's Privacy Protection Act.
- Gramm-Leach-Bliley Act.
- Homeland Security Act.
- Intelligence Reform and Terrorism Prevention Act.
- Writing and Enforcing Online Laws
- The increased use of the internet has changed how older laws need to be enforced. A good example of this is copyright law and the ability for individuals to illegally download music, movies, books, and other forms of intellectual property.
Let's start with Basics of outlook [PPT ]first Microsoft Outlook is the email client included with the Microsoft Office suite.
It is designed to operate as an independent personal information manager, as an Internet mail client, or in conjunction with the Microsoft Exchange Server for group scheduling, email, and task management.
Outlook allows you to send and receive email messages, manage your calendar, store names and numbers of your contacts, and track your tasks. However, even if you use Outlook every day, you might not know some of the cool things it can do to help you be more productive.
One of the biggest advantages of using MS Outlook is that it can serve the purpose of both, a stand-alone application and also a multi-user software. It can be used by an individual as an email client-server and also by an organization which requires shared features like a mailbox, calendar, appointments, etc. Initially, the program was just added as a part of the Office suite which could be installed in a computer system. Later on, various other versions were released which made Outlook compatible with mobile phones, laptops and other android and Mac devices.
Now we have to enter into the Intermediate level of Outlook
Outlook 97 Released on January 16, 1997. It had replaced the existing Microsoft’s email clients including Exchange Client, Schedule+ etc.
Outlook 98. Released on June 21, 1998. It was freely distributed with books and magazines to cope up with the latest Internet standard Involved usage of HTML mail
Outlook 2002. Released on May 31, 2001 Introduced in Office XP Brought in new features like coloured tables, hyperlinks, autocomplete and MSN messenger integration
Outlook 2003. Released on June 27, 1999. Desktop alerts for emails were introduced. Filtering of mails to skip spam. Expandable distribution list. Unicode support
Outlook 2007, Released on January 27, 2007. Feature to preview the attachments was introduced. Excel, Word, PowerPoint files were now supported by Outlook. Features like calendar sharing, export of PDF and XLS files, unified messaging support, etc. were also added to the application.
Outlook 2010. Released on July 15, 2010, Group messages could now be shared. The feature of social connector, where the files could be shared on social networking platforms was introduced
Outlook 2013, . Released on January 29, 2013. A reminder to ask the user to attach files with mail was introduced. People hub, Compression of Outlook data file. Improvement in start up performances
Outlook 2016. Released on September 22, 2015. Almost similar features, only cloud computing was added.
Outlook 2019. Released on September 24, 2018. Filtering and sorting of mails became easier. Supported a focussed inbox. Multiple time zones could be added.
Apart from these, versions which incorporated mobile (android and mac) versions were also released. This move was extremely appreciated as for Organisations it acted as a benefit. They also came up with some commercial features which became more handy and easily accessible using the mobile phone version.
For those are not much familiar with Computer Knowledge and wish to learn more about the various programs, applications and terms related to Computer Awareness, refer to the links given below:
Functions of MS Outlook
This program of the MS Office suite allows you to send emails, arrange meetings, give appointments, etc. can be used by a single individual or a group of people.
The major functions of MS Outlook have, however, been discussed in detail below:
It makes communication easy and sending emails is just a click away. Various attachments in different formats can be added to these mails
Since it is an organising and managing application, it provides features to set up appointments and meeting using calendar and setting up reminders for the same
What are the limitations of using MS Outlook?
Ans. Following are the limitations of using MS Outlook:
- It is less flexible.
- Information is saved on the Microsoft server.
- There is a limitation to the number of emails that can be sent per day
- Financial Management
- Cost issues
- With Microsoft Outlook on your PC, Mac or mobile device, you can organize email, share your calendar, schedule meetings, and share files.
- Outlook can be used as a standalone personal email software, and business customers can use Outlook as multiuser software.
- MS Outlook is a personal information manager which was introduced in 1997 by Microsoft.
- Microsoft Outlook is an application you pay for and install on your device.
Social media are interactive technologies that facilitate the creation and sharing of information, ideas, interests, and other forms of expression through virtual communities and networks.
Topics to be covered in Social Media computing skills
Social Media Marketing is also one of the most important aspects or sub-topics of digital marketing.
Businesses can utilize all of the major social media platforms (Facebook, Twitter, Instagram, Youtube) to connect with the audience and convince them to a call to action.
The majority of traffic is supposedly coming from social media, hence maintaining a good social media strategy is important.
Social Media Marketing covers all these aspects and trains you to optimize your social media platforms for better traffic and revenue generation.
The major sub-topics covered under the Social Media Marketing are:
Definition of Social Media Marketing & social media
Blogging
Blogging Article Marketing
Guest Blogging
Social Networking
Video Creation & Sharing
Use of Different Social Media Platforms
Content Creation
Content Strategy
Content Marketing Tools
- It scales easily.
- It is cost-effective.
- It provides a direct line to engage with your customers.
- Results can be quickly and transparently measured and analyzed.
- It provides an avenue for you to learn from your customers, market, and other industry players. Digital marketing examples:
The ride-sharing app Uber has disrupted the taxi services industry since it launched its first ride in 2010. Uber uses Facebook, Instagram, and Twitter as its main digital marketing channels, using social media to engage with customers and propagate positive, inclusive messaging about connectivity and social awareness. By connecting its messaging to cultural issues, customers feel a greater sense of connection to the brand.
The online movie streaming app Netflix has expanded into 190 countries worldwide. Netflix uses Facebook, Twitter, Pinterest, YouTube, and Instagram and actively engages with customers across its social media channels. The phrase "Netflix and chill" has become a popular part of global pop culture. The brand creates relatable, culturally relevant, and entertaining social content, sometimes crowdsourcing product improvement decisions from customers using polls.
Social media is a great way to reach a specific, targeted audience and connect directly with customers, potential customers, and partners. Which social media platform(s) you use depends on who you want to target.
Every social media platform features different types of content, but all are very video/image focused. So, as you create content, always keep in mind how you want to distribute it through social media, and then adjust accordingly.
- Emails
- SMS
- In-app/push notifications
- Social media (Instagram, TikTok, LinkedIn, Facebook, Snapchat, Twitter, Pinterest)
- Audio (Spotify, Pandora, Apple Music)
- Digital advertising (banner ads, pop-up ads)
- Video (YouTube, Netflix, Hulu) Digital marketers use digital media to connect with customers. so, digital marketing is the strategy and digital media is the means.
A person who writes a blog or a weblog is a blogger. Blogging is the act of posting content on a blog.
The main purpose of blog is to convey messages about events, announcements, needs, review etc. Blogs are usually managed using a web browser and this requires active internet connection.
Blog
A blog is a website or a web page,in which an individual records opinion links to other sites on regular basis. A blog content is written frequently and added in a chronological order.
It is written online and visible to\everyone. A typical blog combines text,images and links to other blogs, web pages and other media related to its topic.In education, blogs can be used as instructional resources.
These blogs are referred to as edublogs. The entries of blog are also known as posts.A person who writes a blog or a weblog is known as blogger. Blogging is the act of posting content on a blog.
There are some popular websites which offer blog service as follows
- Joomla
- WordPress.com
- Drupal ! Blogger
- Tumblr ! Weebly
- Blogger.com
Video marketing
- Blog posts
- photos
- infographics
- videos
- podcasts
- presentations
- e-books
- white papers
- e-newsletters
- webinars
- search engine optimization or SEO
- social media marketing
- Teleconferencing is a generic term used to describe electronic communication between two or more individuals. Traditionally, teleconferencing involved a conference between two or more people, held over the telephone. The individuals typically used a speaker telephone on both ends, allowing for synchronous communication.
- Now!. A teleconference is a live audio or audiovisual meetings with two or more participants. With the ability to teleconference, remote teams in an organization can collaborate and communicate, even when geographically dispersed. The process involves technology more sophisticated than a simple two-way phone connection.
Web conferencing
Web conferencing is a broader term that encapsulates all types of audio and video interaction that happens over the internet. Audio conferencing, video conferencing, screen sharing, and webinars are all generally referred to as web conferencing.
When to use web conferencing:
- 1. Business-wide meetings
- 2. Online events
- 3. Training sessions
Video conferencing
Video conferencing refers to when two or more people connect over the internet and interact with live video and audio. Though this is a type of web conferencing, video conferencing usually refers to remote collaboration within a small group using real-time audio and video feed.
When to use video conferencing:
- 1. Remote team meetings
- 2. Personal video calls
- 3. Feedback sessions
Q #1) What is Web Conferencing Software?
Answer: It is a platform that allows individuals to conduct meetings online, via video or audio. They are also known for their video conferencing capabilities.
Such tools are also ideal for triggering remote sessions for file sharing, VoIP, screen sharing, and instant messaging. This is a major reason these tools have become so integral to the functioning of businesses that harbor remote workforces.
Q #2) What is the most used web conferencing software?
Answer: The web conferencing software market today has become really crowded. As such, it can become really challenging to find web conferencing software that best caters to your specific requirements.
In hindsight, we would say that tools like Zoom and Skype are some of the most popular web conferencing software we have today. Their popularity, however, in no way serves as a testament to their competency.
Q #3) What is an example of a web conferencing tool?
Answer: As mentioned earlier, there are multiple web conferencing tools out there. The most prominent of the bunch are the ones recommended below:
- Zoho Meeting
- Zoom
- Whereby
- Livestorm
- Google Meet
Answer: There are three major types of web conferencing tools.
They are as follows:
- Web meeting
- Webinar
- Webcast
Answer: Web conferencing has completely changed the world as we know it. That mostly has to do with the following benefits it offers:
- Saves time in meetings.
- No commute is necessary, thus reducing travel costs.
- Remotely sharing resources like PDFs, presentations, and spreadsheets.
- Increases work productivity.
- Make meetings more engaging with the use of graphics.
Some popular known impressive tools for web conferencing:
- Zoho Meeting (Recommended)
- Livestorm
- Zoom
- Whereby
- Livestorm
- Google Hangouts
- Dialpad Meetings
- Slack
- Skype
- Google Meet
- Microsoft Teams
- TrueConf Online
- Lifesize
- FreeConference
- Facebook Live
- Personal computer
- Telephone lines or satellite hook-up
- Monitor
- Microphone
- Webcam
- Speakers
- Let all branches know what is going on.
- Easy communication over long distance
- Saves time, money, and energy.
- Reduces face to face interactions.

























































No comments:
Post a Comment
If you have any query or doubt, please let me know. I will try my level best to resolve the same at earliest.